between
______________________________
______________________________
- Responsible - hereinafter also referred to as: "Controller"
And
imito AG
Flüelastrasse 31
8047 Zurich,
represented by Chrysanth Sulzberger
- Contractor - hereinafter also referred to as “Processor”
each a ‘party’; together ‘the parties’
HAVE AGREED on the following Data Processing Agreement (DPA) in order to meet the requirements of the GDPR and to ensure the protection of the rights of the data subject.
This Data Processing Agreement sets out the rights and obligations of the data controller and the data processor, when processing personal data on behalf of the data controller in the course of the activities specified or required in the service provision Agreement (“Main Agreement”) signed by the parties.
The clauses of this Agreement shall take priority over any similar provisions contained in other agreements between the parties.
“GDPR” means the General Data Protection Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data.
”Applicable Data Privacy Law” means such privacy and personal data laws and all other legislation (including regulations and mandatory rules) applicable to the personal data processing conducted under this Data Processing Agreement, including national legislation and EU Regulation, as amended from time to time.
“Personal Data” means any information relating to an identified or identifiable individual where such information is contained within Customer Data and is protected similarly as personal data or personally identifiable information under applicable Data Protection Law.
“Data Subject” means the individual to whom Personal Data relates.
“Controller” means the natural or legal person, public authority, agency or other body which, alone or jointly with others, determines the purposes and means of the Processing of Personal Data.
“Processor” means a natural or legal person, public authority, agency or other body which processes Personal Data on behalf of the Controller.
“Processing” means any operation or set of operations which is performed on Personal Data, encompassing the collection, recording, organization, structuring, storage, adaptation or alteration, retrieval, consultation, use, disclosure by transmission, dissemination or otherwise making available, alignment or combination, restriction or erasure of Personal Data.
“Instruction” means the written, documented instruction, issued by Controller to Processor, and directing the same to perform a specific action with regard to Personal Data (including, but not limited to, depersonalizing, blocking, deletion, making available).
“Personal Data Breach” means a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to, Personal Data transmitted, stored or otherwise processed.
The scope of the data-processing agreement is the execution of the activities regulated in the main contract.
The processing of personal data may solely be done by Processor in order to fulfill Processor’s responsibilities under this Data Processing Agreement.
The Processor shall not use the personal data for any other purposes than those set out in this Data Processing Agreement.
The duration of this agreement (term) corresponds to the duration of the main contract. It ends without the need for a separate notice of termination as soon as the main contract is terminated, ends or expires for any other reason.
In connection with the Data Processor’s delivery of the Main Services to the Data Controller, the Data Processor, on behalf of the Data Controller, will process certain categories and types of personal data pertaining to natural persons.
The Data Processor only performs processing activities that are necessary and relevant to perform the Main Services.
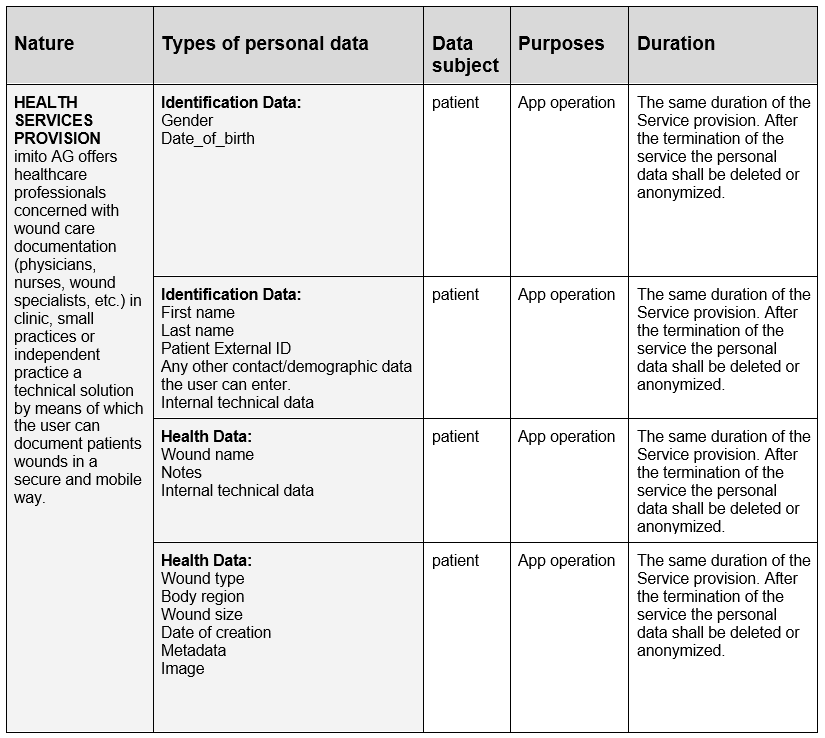
The processing’s nature, purposes, types of personal data and the categories of data subjects processed by the Data Processor on behalf of the Data Controller are:
The contractually agreed data processing is carried out in Switzerland or in a member state of the European Union or the European Economic Area. The transfer of personal data from the EU / EEA to Switzerland is based on the adequacy decision 2000/518/E. Any transfer to another third country requires the prior consent of the client and may only take place if the special conditions of art. 44 et seq. GDPR are fulfilled.
The Data Processor may only act and process the Personal Data in accordance with the documented instruction from the Data Controller (the “Instruction”), unless required by law to act without such instruction.
The Instruction at the time of entering into this Data Processor Agreement (DPA) is that the Data Processor may only process the Personal Data with the purpose of delivering the Main Services as described in the Main Service Agreement. Subject to the terms of this DPA and with mutual agreement of the parties, the Data Controller may issue additional written instructions consistent with the terms of this Agreement. The Data Controller is responsible for ensuring that all individuals who provide written instructions are authorized to do so.
The Data Controller guarantees to process Personal Data in accordance with the requirements of Data Protection Laws and Regulations. The Data Controller’s instructions for the processing of Personal Data shall comply with Applicable Law. The Data Controller will have sole responsibility for the accuracy, quality, and legality of Personal Data and the means by which it was obtained.
The level of security shall take into account that the processing involves personal data which are subject to Article 9 GDPR on ‘special categories of personal data’ which is why a ‘high’ level of security should be established.”
The data processor shall hereafter be entitled and under obligation to make decisions about the technical and organisational security measures that are to be applied to create the necessary (and agreed) level of data security.
The data controller is responsible for ensuring that the processing of personal data takes place in compliance with the GDPR (see Article 24 GDPR), the applicable EU or Member State (References to ”Member States” made throughout the DPA shall be understood as references to “EEA Member States”) data protection provisions and the DPA.
The data controller has the right and obligation to make decisions about the purposes and means of the processing of personal data.
The data controller shall be responsible, among others, for ensuring that the processing of personal data, which the data processor is instructed to perform, has a legal basis.
The data processor shall process personal data only on documented instructions from the data controller, unless required to do so by Union or Member State law to which the processor is subject. Such instructions shall be specified in appendices A and C. Subsequent instructions can also be given by the data controller throughout the duration of the processing of personal data, but such instructions shall always be documented and kept in writing, including electronically, in connection with the DPA.
The data processor shall immediately inform the data controller if instructions given by the data controller, in the opinion of the data processor, contravene the GDPR or the applicable EU or Member State data protection provisions.
The Processor has implemented, as far as necessary, the technical and organizational measures according to Art. 32 GDPR prior to the award of the contract. The corresponding proof will be provided to the client on request without culpable hesitation. Insofar as the inspection or an audit of the client reveals a need for adjustment, this must be implemented by mutual agreement.
The Processor must provide the security in accordance with Art. 28 (3) point (c) - 32 GDPR, in particular in connection with Art. 5 (1-2) GDPR. Overall, the actions to be taken are data security measures and to ensure a level of protection appropriate to the level of risk with regard to the confidentiality, integrity, availability and resilience of the systems. In this context, the state of the art, the implementation costs and the type, scope and purpose of the processing as well as the different probability and severity of the risk for the rights and freedoms of natural persons within the meaning of Art. 32 (1) GDPR must be taken into account.
The technical and organizational measures are subject to technical progress and further development. In that regard, the Processor is allowed to implement alternative adequate measures. At the same time, the safety level of the specified measures must not be undershot. Significant changes must be documented.
The Processor may not correct, delete or restrict the processing of the data processed on behalf of the contract, but only on the basis of documented instructions from the Controller. Insofar as a data subject directly addresses the Processor in this regard, the Processor will immediately forward this request to the Controller.
Unless otherwise provided for, erasure concept, right to be forgotten, rectification, data portability and information to be provided by the client. The Processor shall only contribute to the exercise and enforcement of the said data subjects’ rights to documented instructions from the Controller within the scope of the powers assigned to him.
In addition to complying with the provisions of this contract, the Processor has statutory obligations in accordance with Art. 28 to 33 GDPR; in this respect, the Processor guarantees in particular compliance with the following requirements:
The maintenance of confidentiality in accordance with Art. 28 (3) sentence 2 lit. b, 29, 32 (4) GDPR. In performing the work, the Processor shall only employ employees who are bound to confidentiality and who have previously been made familiar with the provisions on data protection relevant to them. The Processor and any person subordinate to the Processor who has access to personal data may process such data exclusively in accordance with the instructions of the Controller, including the powers granted in this Agreement, unless they are legally obliged to process such data.
The implementation of and compliance with all technical and organisational measures required for this contract in accordance with Art. 28 (3) sentence 2 lit. c, 32 GDPR, as described in Annex 1.
The Controller and the Processor (as well as their representatives) shall cooperate with the supervisory authority on request in the performance of their duties.
Immediate information of the Controller about control actions and measures of the supervisory authority, insofar as they relate to this agreement. This shall also apply where a competent authority, in the course of administrative or criminal proceedings, investigates the processing of personal data in connection with the processing of orders at the Processor.
Insofar as the Controller himself is subject to inspection by the supervisory authority to administrative or criminal proceedings, to liability of a data subject or third party or to any other claim relating to the processing of personal data in connection with the processing at the Processor’s premises, the Processor shall use his best endeavours to support him.
The Processor will regularly review internal processes and technical and organizational measures to ensure that processing within his area of responsibility complies with the requirements of applicable data protection law and ensures the protection of the data subject's rights.
Subcontracting relationships within the meaning of this regulation are to be understood as those services which relate directly to the provision of the main service.
The data processor shall meet the requirements specified in Article 28(2) and (4) GDPR in order to engage another processor (a sub-processor).
The data processor shall therefore not engage another processor (sub-processor) without the prior general written authorisation of the data controller.
The data processor has the data controller’s general authorisation for the engagement of sub-processors. The data processor shall inform in a written form the data controller of any intended changes concerning the addition or replacement of sub-processors at least 15 days in advance, thereby giving the data controller the opportunity to object to such changes prior to the engagement of the concerned sub-processor(s).
Where the data processor engages a sub-processor for carrying out specific processing activities on behalf of the data controller, the same data protection obligations shall be imposed on that sub-processor by way of a contract or other legal act under EU or Member State law, in particular providing sufficient guarantees to implement appropriate technical and organisational measures in such a manner that the processing will meet the requirements of the DPA and the GDPR.
The data processor shall therefore be responsible for requiring that the sub-processor at least complies with the obligations to which the data processor is subject pursuant to this Agreement and the GDPR.
If the subProcessor provides the agreed service outside the EU / EEA, the Processor shall ensure that the data protection law is admissible by taking appropriate measures.
A copy of such a sub-processor agreement and subsequent amendments shall – at the data controller’s request – be submitted to the data controller, thereby giving the data controller the opportunity to ensure that the same data protection obligations are imposed on the sub-processor. Clauses on business related issues that do not affect the legal data protection content of the sub-processor agreement, shall not require submission to the data controller.
If the sub-processor does not fulfil his data protection obligations, the data processor shall remain fully liable to the data controller as regards the fulfilment of the obligations of the sub-processor. This does not affect the rights of the data subjects under the GDPR – in particular those foreseen in Articles 79 and 82 GDPR – against the data controller and the data processor, including the sub-processor.
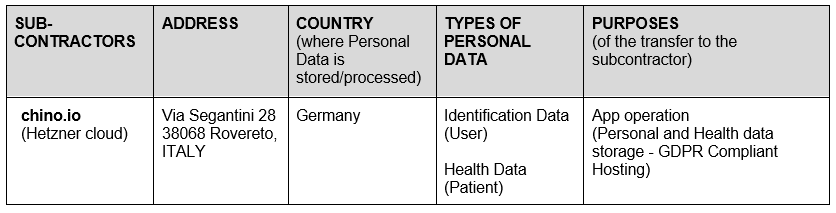
The data controller authorises the engagement of the following sub-processors:
Upon request by a Data Controller, the Data Processor shall make available to the Data Controller all relevant information necessary to demonstrate compliance with this DPA, and shall allow for and reasonably cooperate with audits, including inspections by the Data Controller or an auditor mandated by the Data Controller. The Data Controller shall give notice of any audit or document inspection to be conducted and shall make reasonable endeavours to avoid causing damage or disruption to the Data Processors premises, equipment and business in the course of such an audit or inspection. Any audit or document inspection shall be carried out with reasonable prior written notice of no less than 30 days, and shall not be conducted more than once a year.
The Data Controller may be requested to sign a non-disclosure agreement reasonably acceptable to the Data Processor before being furnished with the above.
The costs of the audit will be borne by the Controller.
In case of any personal data breach, the data processor shall, without undue delay after having become aware of it, notify the data controller of the personal data breach.
The data processor shall notify the controller without undue delay after becoming aware of the personal data breach to enable the data controller to comply with the data controller’s obligation to notify the personal data breach to the competent supervisory authority according to Article 33 GDPR.
The data processor shall assist the data controller in notifying the personal data breach to the competent supervisory authority, meaning that the data processor is required to assist in obtaining the information listed below which, pursuant to Article 33(3)GDPR, shall be stated in the data controller’s notification to the competent supervisory authority:
Copies or duplicates of the data are not created without the knowledge of the client. This does not include backup copies, to the extent necessary to ensure proper data processing, and data required for compliance with statutory retention requirements.
Upon termination of the provision of personal data processing services, the Processor shall either delete or return the personal data in accordance with this DPA. The same applies to test and scrap material. The log of the deletion must be submitted on request.
Documentation serving as evidence of orderly and proper data processing must be kept by the Processor according to the respective retention periods beyond the end of the contract. He can hand them over to the client for discharge at the end of the contract.
The Agreement shall become effective on the date of both parties’ signature.
Both parties shall be entitled to require the Agreement renegotiated if changes to the law or inexpediency of the Agreement should give rise to such renegotiation.
The Agreement shall apply for the duration of the provision of personal data processing services. For the duration of the provision of personal data processing services, the Agreement cannot be terminated unless other Agreement governing the provision of personal data processing services have been agreed between the parties.
If the provision of personal data processing services is terminated, and the personal data is deleted or returned to the data controller, the Agreement may be terminated by written notice by either party.
The parties may contact each other using the following contacts/contact points:
The parties shall be under obligation continuously to inform each other of changes to contacts/contact points.
Controller
Processor
Encryption (Logical security control)
Our digital solution relies on our processor Chino.io’s encryption methods in order to address GDPR compliance needs. Chino.io Data Security platform implements encryption of both data in transfer and at rest. Data is transferred via HTTPS, encrypted immediately upon transmission, and stored encrypted. Encryption keys are stored on different servers (according to the state of the art security safeguards)
Pseudonymisation (Logical security control)
Sensitive data and identifiers are stored separately using different data structures and both encrypted at record level.
Logical access control (Logical security control), Authentication and Access Control (or Authorization) via access control policies (also called Permissions)
Authentication: Chino.io API implements two different methods of authentication for administrators and end-users.
Access Control (or Authorization) via access control policies (also called Permissions) provide a granular and flexible control over access to data. All the actions carried out on the data are registered with a specific log creation.
Password (Logical security control)
Passwords protected and managed according to best practices.
Surveillance (Logical security control)
Implement a regular control of logs, based on European DPAs’ guidelines.
Minimising the amount of personal data (Logical security control)
We reduce the volume of data accumulation by only collecting and accessing the personal data that is absolutely necessary for the provision of the service.
Limited Storage Duration (Logical security control)
Appropriate data retention procedures have been adopted.
Managing workstations (Physical Security Control)
Appropriate company and contractor security policies have been adopted.
Processing contracts (Physical Security Control)
We only use subcontractors which are able to provide sufficient guarantees according to the Data Processing Agreements signed with them.
Network security (Physical Security Control)
imito AG relies on Data processor sub-contractors (Google, Hetzner, Zoho). Communication to those system consoles is SSL encrypted.
Security of Data on User’s device (Physical Security Control)
imito AG app do not cache sensible data on the user’s device. The temporary cached data is cleaned after each session.
Organisation (Organisational control)
Internal roles and responsibilities for data protection are clearly defined.
Personnel management (Organisational control)
A permission-based access system is restricting the number of personnel employees accessing personal data.
The proportionality of each access and the data it gives access to, has been assessed.
Relations with third parties (Organisational control)
All third parties who have or could have legitimate access to personal data have been identified.
Their role in the processing (including IT administrators, processors, recipients, persons responsible for processing data and authorized third parties), based on the actions they will perform, has been determined.
Traceability (logging) (Logical security control) and Auditing: all registry operations logs are saved in the database. The system tracks who accesses your data, when it was accessed, and from where.
Operating security (Physical Security Control)
Software updates (operating systems, applications, etc) and application of security corrective control patches are carried out. On level Infrastructure and API security and Applications.
Policy (Organisational control)
Appropriate policies regarding the handling of personal data in the company have been adopted.
Integrating privacy protection in projects (Organisational control)
We implemented privacy by design and by default in our technology and in our projects.
Backups (Physical Security Control)
Regular backups are executed on the database information through chino.io and Zoho.
Maintenance (Physical Security Control)
Physical maintenance of hardware is outsourced to our Data processor sub-contractors.
Physical access control (Physical Security Control)
We rely on our sub-processors to limit the risks of unauthorized persons gaining physical access to the servers where personal data is stored.
Monitoring network activity
imito AG relies on Data processor sub-contractors (Google, Hetzner, Zoho) for active unauthorised access control.
Hardware security (Physical Security Control)
imito AG relies on Data processor sub-contractors (Google, Hetzner, Zoho) hardware & workstation security in places.
Appropriate policies have been adopted for our contractors.
Clamping down on malicious software (Physical Security Control)
On the server-side we rely on our partners data-processor to fulfill best practices as up-to-date antiviruses and well-configured firewalls.
On employees and contractors’ workstations there is the employment of security programs (virus scanners, firewalls, encryption programs).
Website security (Physical Security Control)
Appropriate measures to protect the backend have been adopted.
Avoiding sources of risk (Physical Security Control)
The processed data are not stored in any foreign country that cannot guarantee an adequate level of data protection.
Protecting against non-human sources of risks (Physical Security Control)
We rely on our subcontractors (Google, Hetzner, Zoho) for the prevention, continuity, and protection of the systems.
Managing privacy risks (Organisational control)
Risk assessments and control policies of risks that processing performed operations pose on data protection and the privacy of data subjects, have been carried on and clearly analyzed and defined.
Managing personal data violations (Organisational control)
Appropriate data breach procedures have been adopted.
Supervision
The most sensible processes will be inspected by internal stakeholders to guarantee continuous improvement.
Nous utilisons des cookies pour améliorer l’expérience utilisateur sur notre site Web.
Plus d’informations sur notre Politique de confidentialité.